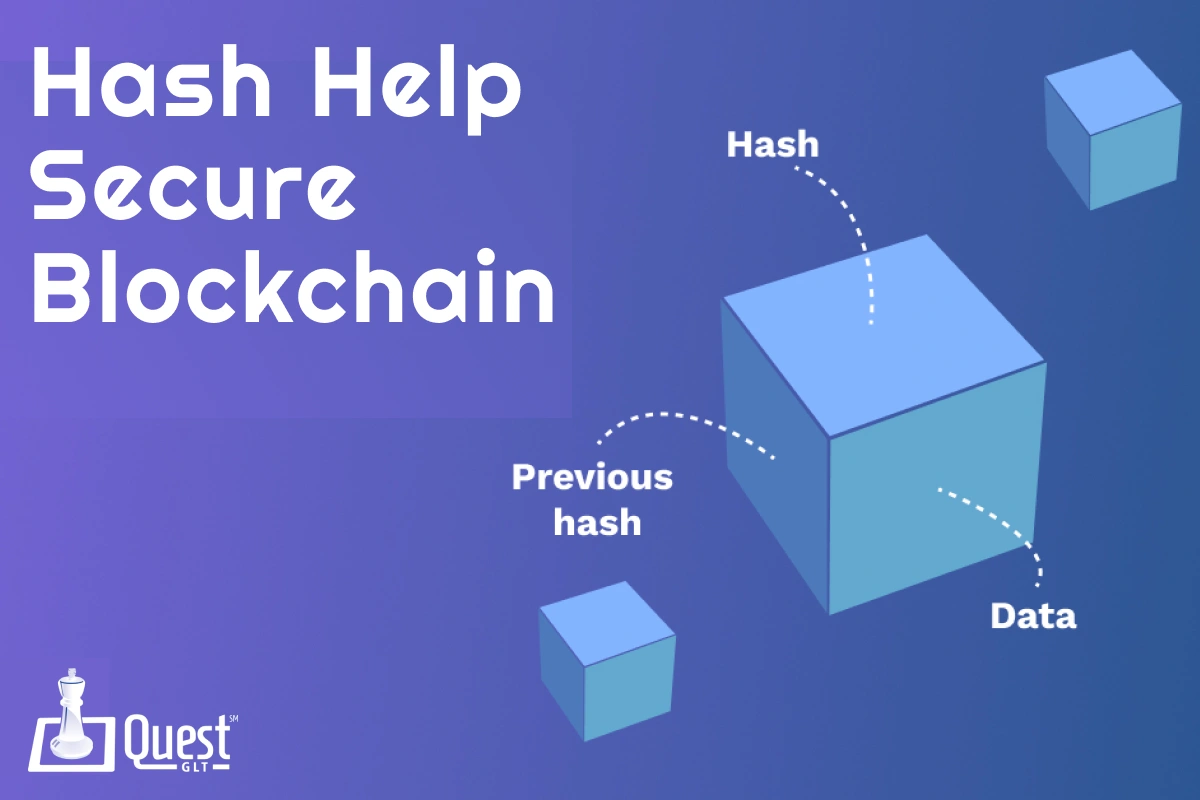
Curious to know how blockchain technology can operate so securely? As a result, one of its key elements is hashing, which contributes significantly to its overall security. A hash is a digital fingerprint of a block of information that is unique to the block of data in the blockchain. It is designed with the help of advanced mathematical processes that convert the source into a specific word and number sequence. After the data is processed by the hashing algorithm, it becomes very difficult to retrieve the original data from the hash. Therefore, it is very complex to refine blockchain data without de-identifying it.
Each new block added to the blockchain contains a hash of the previous block, linking them together and creating an unbreakable chain secured by the hashes. This means that any effort to invade one block on the chain will lead to the alteration of every subsequent block in the chain, which is extremely difficult and very unlikely to go unnoticed.
The world accepts blockchain technology for the variety of its benefits. Hence, we should know blockchain technology and the foundation upon which it is built. Hashing is one of the cornerstones of blockchain; it is the root cause of data integrity and security. However, to grasp it, first, get a grasp of how hashing works and why it is so pivotal to blockchain technology. And the most important question is: How does a hash help secure blockchain technology? The blog will answer all your questions. Therefore, first, let us clarify what “Hash” means.
Important Learnings
-
Hash functions are crucial for safe and efficient blockchain networks, as they offer data integrity, immutability, and transaction verification.
-
Cryptographic hash functions such as SHA-256 safeguard private keys and digital signatures while stopping conspiracy and centralization.
-
It is an important part of consensus mechanisms that validate transactions and add novel blocks to the blockchain.
What is Hashing in Blockchain?
The validation of transactions conducted on both public and private chains is based on hashing. It prevents unauthorised change by keeping data safe and uneditable. Hashing is used in different parts of a blockchain system to guarantee data integrity. When a new block is added, the hash of the current block is included along with the block header. Blockchain technology uses hashing to reinforce the reliability, security, and immutability of the offered transactions. Let us discuss the fundamental mechanisms underpinning hashes that make the blockchain secure.
The Fundamentals of Hashing in Blockchain
The cryptographic hash function is the core of blockchain technology, an important tool that enables data transformation into digestible or fixed-length hash values. This cryptographic hashing algorithm ensures that even minor changes in the input data produce different hash values. This unique digital imprint, an important part of blockchain technology, increases the security and integrity of data.
Many aspects of blockchain technology depend on hashing functions, including:
-
Ensuring data integrity
-
Rendering blocks are immutable.
-
Verifying transactions.
-
Protecting private keys and digital signatures.
-
Transactions are validated using block hashes in consensus systems.
Now that you understand this, let’s take a deeper look into the fundamentals of hashing in blockchain.
-
Data Integrity
Cryptographic techniques known as hash functions take an input (or message) and output a fixed-length character string, which is called the hash value or digest. Every block in a blockchain carries a hash of the block before it. This initiates a chain of blocks, and if the data in one block were to change, the hash of that block and all the blocks after it would also need to change. The integrity of the entire chain is guaranteed by this dependency.
-
Immutability
It becomes practically impossible to change any information in a block once it is added to the blockchain without altering all subsequent blocks. This is so because every block’s hash is a unique representation of its data. The blockchain offers a robust layer of security, as it takes a lot of computational power to change the hash of a block and all linked blocks.
-
Tamper Resistance
A strong hash function should be highly unlikely to obtain the same hash value when two different inputs are used. This is known as tamper resistance. This ensures that every block in the context of a blockchain has a distinct equivalence. The blockchain's integrity may be jeopardised if collisions are frequent since they could result in possible vulnerabilities when various sets of data yield the same hash.
-
Consensus Protocols
Consensus mechanisms, like Proof of Work (PoW) or Proof of Stake (POS), are often used in blockchain networks to validate and append new blocks to the chain. A crucial component in these mechanisms is hash functions. For example, in PoW, miners compete to discover a hash value that meets specific standards. This computational problem maintains the network’s security and decentralisation in addition to including new blocks.
-
Private keys and digital signatures
In blockchain public-key cryptography, hash functions are widely used. Hash functions are implemented to generate public keys and digital signatures, which gives participants a secure way to transact and verify asset ownership. This cryptographic approach provides an additional line of defence against fraud and illegal access.
Understanding Hash Functions
Imagine there was a magical box that could accept any input of any size or any content and transform it into an output of a fixed length. Essentially, this box is a hash function. In blockchain, hash functions are one-way mathematical operations that convert any size of input data into an output with a fixed length while making it exceedingly challenging to impossible to detect the original input.
Different Hashing Algorithms in the Blockchain
Although hashing is a fundamental component of all blockchain systems, other algorithms may be employed. Every hashing algorithm is different from the others and is selected according to the requirements of the specific blockchain.
-
SHA-256:
It generates a 256-bit hash and is known for its robust security features. It is known for its computational complexity and high attack resistance, which makes it ideal for mining proof-of-work.
-
ETHASH:
Optimized for GPU mining, this is designed to be ASIC-resistant. This was a purposeful decision to avoid mining consolidation. As that requires more memory than hash, it is memory-hard and contributes to the democratisation of mining.
-
SCRYPT:
Faster and less resource-intensive than SHA-256, yet with similar functionality. While scrypt requires more memory than Ethash, which makes it more manageable for individual miners with less capable gear.
-
X11:
One of the more complex algorithms combines 11 distinct hash functions. X11 is renowned for producing less heat during mining and for being energy-efficient.
-
CRYPTONIGHT:
Egalitarian mining and privacy are priorities. It allows for more equal mining across different types of hardware, including CPUs, and is intended to be resistant to ASICs.
-
BLAKE2:
Blake2 is an alternative to SHA-256 that offers similar levels of security but with faster processing times and is well-known for its great speed and efficiency.
Each of these algorithms provides a distinct balance between security, speed, and accessibility while still fulfilling the fundamental purpose of hashing, which secures data and ensures its integrity. A blockchain’s functionality can be affected by the algorithm used, particularly in terms of its resistance to centralised control and mining processes.
The Differences Between Proof of Work (Pow) and Hashing
Both hashing and proof of work (PoW) form an essential part of the technology of blockchain, each having its functions.
Hashing is the basic building block of cryptography and computers. It refers to the process of converting the incoming data, for instance, transaction details, into a fixed-length digit string, namely a hash. To keep the data on the blockchain consistent and secure, hash functions are used for their speed, determinism, and sensitivity to any changes in the input data. Use a secure link between each block's data and the hash of the previous block by including a unique hash of both.
Nevertheless, Proof of Work (PoW) performs the two functions of adding new blocks to the chain and validating transactions in some blockchain networks, such as Bitcoin. Nowadays, miners are in the process of solving complex mathematical puzzles that would require them to consume a lot of computing power. The first miner to solve the given problems wins the right to add a new block to the chain and gets a reward from the network in cryptocurrency. Through the increase in the cost and duration of network attacks, PoW tries to keep out spamming and fraudulent behaviour.
In short, hashing is a principal requirement for the development of safe data representations, but PoW employs hashing in its mechanisms for the preservation of the blockchain, the generation of new blocks, and the verification of transactions. Besides, hashing is indispensable for proof of work (PoW), but it has wider applications in computer science and information security.
Problems and Restrictions of Blockchain Hashing
Hashing contributes a significant value in the blockchain technology field, but some problems and restrictions are the result.
-
Scalability Issues: Hash functions are instrumental in the maintenance of consistent and smooth transactions in the mining processes of blockchain systems. Hashing, which speeds up the transaction process, may not be effective for growing networks and a vast volume of transactions as compared to transactions that are held on exchanges. Hashing puzzles that are strong in terms of computing power occupy most resources and eventually cause lags in real-time transaction processing, complicating further network development.
-
Quantum Computing Threat: The real hacks that have been used in blockchain creation are a huge obstacle to the development of quantum computers. These machines use very sophisticated algorithms to crack the codes, which are far more sophisticated than the usual hash functions. This could put the security they offer today at stake. This might make the encryption protocols of blockchains viewed as easy to cheat or not so sound.
-
Energy Use in Mining: PoW blockchains, e.g., Bitcoin, are energy-hungry networks that use a lot of electricity and CPU. This is mainly a hash. The main emissions of mining that deal with climate change are carbon; hence, there have been concerns about environmental sustainability. It causes the energy consumption of PoW blockchains to go up, which becomes a sustainability issue and stimulates experts to discover greener consensus mechanisms.
-
51% Attacks: Although the blockchain network provides a wide range of advantages, one of the present and potential dangers is a 51% assault. This assault, which tends to be more powerful in small networks, could be very destructive to such groups. Among these types of intrusions, an intruder may appropriate the hashing power of more than 50% of the network and hence modify the ledger to suit his ulterior motives. By doing so, double-spend opportunities like blocking new transactions and stopping payments become available, and transactions can be double-spent. It's not possible to regain the confidence of the customers with double-spending on the network and the ecosystem.
-
Collision Resistance: Although the hash function as such is made to minimise the possibility that two different inputs would elicit the same output, it would be mistaken to assume that these functions prevent 100% collision resistance. Although it has a small likelihood, it theoretically should come into operation. Hash collisions in the blockchain may lead to fake transactions or blocks with a great number of other problems, but there is hardly a case, even though now it is impossible with state-of-the-art technology.
Bottom Line
This blog explores the most important question: How does a hash help secure blockchain technology? Hashing, viewed as the core component of blockchain, cannot be ignored due to its uses in achieving data integrity and safety—therefore, efficient data management. Blockchain implements immutability and an increased level of protection by first transforming the data into fixed-size unique hashes. Hashing has some obstacles to overcome, such as scalability constraints, quantum computing threats, and environmental issues from high electricity consumption in mining methods. Despite these challenges, the hash function in the blockchain system is still indisputable. Blockchain app development companies are committed to self-improvement, and they work tirelessly to optimise the technique to keep abreast of the evolving needs of blockchain technology. Over time, the imperative to strive for optimisation has enabled hashing to maintain its standing as the foundation of information security and innovation, bolstering the resiliency of blockchain networks around the world.













